Healthcare clearinghouses act as intermediaries that translate, validate, and transmit healthcare data between providers, payers, and other entities.
Under HIPAA, they safeguard protected health information (PHI). This guide details how clearinghouses comply with HIPAA regulations, the safeguards they implement, and the technologies they use to stay compliant.
Table of Contents
What Is a Healthcare Clearinghouse Under HIPAA?
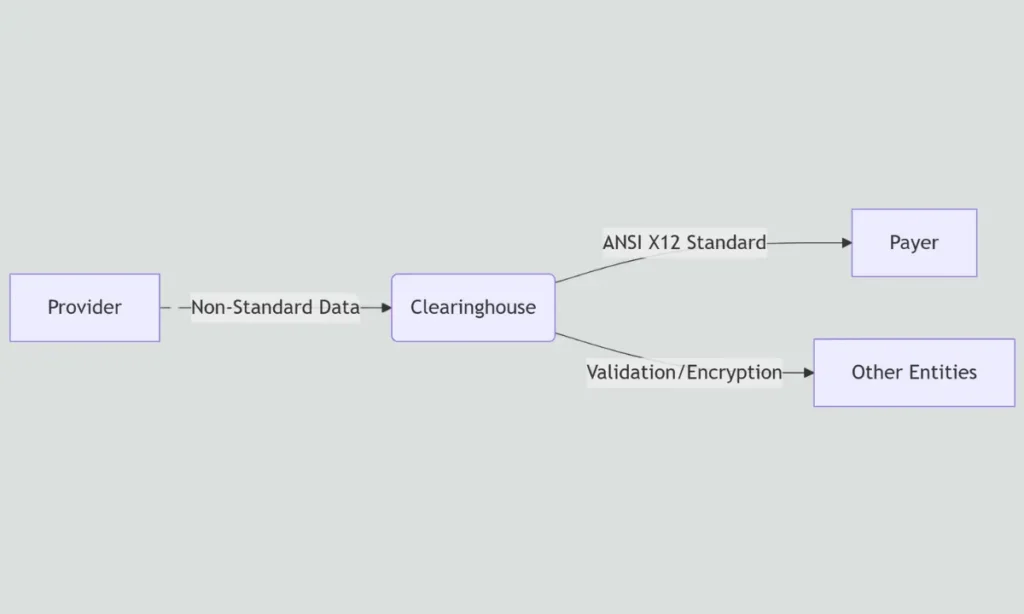
A healthcare clearinghouse processes non-standard healthcare data into standardized, HIPAA-compliant formats (e.g., ANSI X12) before transmitting it to another entity.
Key Functions of a Clearinghouse:
- It translates non-standard formats (e.g., proprietary EMR formats) into standard ANSI X12 (e.g., 837 for claims, 835 for remittance advice).
- Also, it validates data for HIPAA transaction compliance, including correct fields, codes, and required elements.
- Securely routes transactions between providers, payers, and other entities.
HIPAA Status:
A clearinghouse is considered a:
- A clearinghouse is always HIPAA-covered when it conducts standard transactions (e.g., submitting claims to insurers).
- It acts as a Business Associate (BA) only when performing services for another covered entity (e.g., processing data for a hospital under a contract).
Clearinghouse Roles vs. HIPAA Compliance Requirements
| Role | Compliance Obligation | Additional Notes |
|---|---|---|
| Data Translator | Must comply with HIPAA Transactions & Code Sets (TCS) Rule (e.g., ANSI X12 standards). | Ensures data is formatted correctly for claims (837), payments (835), etc. |
| PHI Processor | Must secure PHI per HIPAA Privacy Rule & Security Rule (administrative, physical, technical safeguards). | Includes encryption, access controls, audit logs, and breach notification. |
| Business Associate (BA) | Requires a signed Business Associate Agreement (BAA) if handling PHI on behalf of a Covered Entity. | Applies only when performing services for another Covered Entity (e.g., a hospital or insurer). |
| Covered Entity | Must follow all HIPAA rules (Privacy, Security, Breach Notification, TCS) when conducting standard transactions. | A clearinghouse is always a Covered Entity when submitting transactions directly (e.g., claims to a payer). |
What HIPAA Rules Apply to Clearinghouses?
Clearinghouses must comply with four key HIPAA rules to manage PHI legally:
- Privacy Rule: Limits PHI use and mandates individual rights (e.g., access, corrections).
- Security Rule: Requires physical, administrative, and technical safeguards (e.g., encryption, access logs).
- Breach Notification Rule: Mandates breach disclosure within 60 days (to individuals, HHS, and media for significant breaches).
- Transactions Rule: Standardizes electronic data interchange (EDI) in ANSI X12 formats (e.g., 837 for claims).
Bullet List: Key Compliance Domains
- TLS 1.2+ and AES-256 encryption are used for data security.
- Maintenance of detailed system audit logs (retained for 6+ years).
- Mandatory annual HIPAA training for all employees handling PHI.
- Signed Business Associate Agreements (BAAs) when servicing covered entities.
How Do Clearinghouses Protect PHI from Security Threats?
Clearinghouses implement layered security controls to prevent unauthorized access, breaches, and misuse of PHI.
Core Security Measures:
- Encryption Protocols: TLS 1.2+ secures data in transit; AES-256 encrypts data at rest.
- Access Control: Role-based access control (RBAC) and multi-factor authentication (MFA) for all systems.
- Physical Safeguards: Restricted access to server rooms, badge-only entry, video surveillance, and environmental controls.
- Audit Controls: All PHI access is logged with user IDs/timestamps, monitored in real-time, and reviewed quarterly.
PHI Protection Measures
| Risk | Mitigation Strategy |
|---|---|
| Unauthorized Access | Role-based access control (RBAC) + mandatory MFA for all systems |
| Data Breaches | End-to-end encryption (AES-256 at rest, TLS 1.2+ in transit) + regular penetration testing |
| Insider Threats | Comprehensive staff audits + automated log review systems with AI anomaly detection |
Why Are Business Associate Agreements Essential for Clearinghouses?
Under HIPAA, any clearinghouse acting as a business associate must sign a BAA with each covered entity it supports.
Key Roles of a BAA:
- Establishes legal responsibility for PHI protection under HIPAA rules
- Defines obligations for breach notification and data misuse remediation
- Extends compliance requirements to all subcontractors handling PHI (chain of trust)
- Limits liability by clearly defining each party’s responsibilities
Bullet List: Must-Have BAA Clauses
- Permitted vs prohibited PHI uses (specific business purposes only)
- Breach notification timeframes (typically 60 days maximum)
- Covered entities’ audit rights for compliance verification
- Data return/destruction requirements at contract termination
- Subcontractor management rules ensure equal protection downstream
How Do Clearinghouses Implement the HIPAA Security Rule?
Clearinghouses meet HIPAA Security Rule requirements through structured safeguards across three domains.
1. Administrative Safeguards:
- Conduct comprehensive risk assessments annually and after significant system changes.
- Train staff in HIPAA compliance and data handling with documented records.
- Establish contingency plans for data backup and disaster recovery.
2. Physical Safeguards:
- Secure server infrastructure with 24/7 surveillance and badge-only access.
- Control workstation and device use through asset management policies.
- Implement visitor logs and escort requirements for unauthorized personnel.
3. Technical Safeguards:
- Assign unique user IDs with role-based permissions.
- Employ SIEM (Security Information and Event Management) tools for real-time threat monitoring.
- Enable automatic session timeouts after 15-30 minutes of inactivity.
- Encrypt all ePHI (AES-256 at rest, TLS 1.2+ in transit).
Security Rule Compliance Checklist
| Requirement | Implementation Strategy |
|---|---|
| Risk Analysis | Annual vulnerability scans + quarterly risk assessments + reassessment after system changes |
| Access Controls | RBAC + MFA (enforced for all users) + least privilege principle + automatic account lockouts after failed attempts |
| Audit Controls | Real-time log monitoring via SIEM tools + 90-day log retention + monthly review of access patterns |
| Data Integrity | Cryptographic hash verification + write-once-read-many (WORM) storage for audit logs |
| Transmission Security | TLS 1.2+ encryption for all data in transit + certificate-based authentication |
What Are the Most Common Compliance Challenges for Clearinghouses?
Many clearinghouses encounter technical and operational hurdles that complicate HIPAA compliance.
Common Challenges:
- Legacy system integration: Outdated software incompatible with ANSI X12 standards (e.g., non-EDI formats)
- Third-party risk management: Vendors/subcontractors with inadequate security controls (missing BAAs, weak encryption)
- Audit preparedness: Difficulty maintaining real-time compliance documentation and access logs
- Workforce training: Ensuring consistent HIPAA awareness across staff and contractors
- Breach response: Meeting 60-day notification deadlines while investigating incidents
Challenges vs. Mitigation Strategies
| Challenge | Solution |
|---|---|
| Data Format Errors | Auto-validation + ANSI X12 schema checks + pre-submission quality gates |
| PHI Exposure | Tokenization + de-identification + strict data minimization policies |
| Vendor Risks | Annual BAA reviews + SOC 2 Type II audits + security scorecard monitoring |
| Audit Readiness | Automated log collection + quarterly mock audits + compliance dashboards |
| Legacy Systems | Phased modernization + EDI translation layers + isolated sandbox testing |
Struggling with HIPAA-Compliant Data Exchange or Medical Billing?
Let Our Medical Billing Company handle your medical billing services and clearinghouse needs. Our HIPAA-certified solutions ensure:
✔ Error-free claims processing with ANSI X12 validation
✔ Military-grade encryption (AES-256 & TLS 1.3) for all PHI
✔ Audit-ready compliance with real-time monitoring and breach protection
Contact Our HIPAA Experts Today
What Technologies Help Clearinghouses Maintain Compliance?
Modern clearinghouses use a tech stack designed to detect, prevent, and report compliance issues.
Key Technologies:
- EDI Validators: Check format compliance in real time.
- HIPAA-Compliant Cloud Platforms: AWS and Azure with encrypted data zones.
- AI-Powered Security: Monitors traffic patterns to detect PHI anomalies.
- ePHI Mapping Tools: Automated inventory systems tracking all PHI locations
Bullet List: Compliance-Enabling Technologies
- SIEM systems with UEBA (User Entity Behavior Analytics)
- Automated audit logging with immutable WORM storage
- Blockchain for transaction non-repudiation (not just verification)
- API gateways with HITRUST-certified authentication
- Robotic Process Automation for error-free medical claims processing
How Do Clearinghouses Collaborate with Other Covered Entities to Ensure Compliance?
Clearinghouses ensure HIPAA alignment across the healthcare data exchange chain.
Collaboration Methods:
1. Standardization Alignment:
- Enforce ANSI X12 formats (837 claims, 835 remittances) with NPI/EIN validation
- Implement shared code sets (ICD-10, CPT, HCPCS)
2. Secure Data Routing:
- TLS 1.2+ encrypted connections for all transactions
- End-to-end transaction status tracking
3. PHI Protection:
- Joint BAAs with breach notification protocols
- Coordinated access controls and audit trails
Inter-Entity Data Flows
| Entity | Shared Compliance Responsibility |
|---|---|
| Provider | • Submit PHI via encrypted SFTP/APIs • Verify patient consent status • Maintain 6-year audit logs |
| Clearinghouse | • Real-time X12 syntax validation • Apply AES-256 encryption during processing • Generate immutable transaction receipts |
| Payer | • Confirm EDI file integrity on receipt • Process clean claims within 30 days • Report rejections with error codes |
What Are the HIPAA Penalties That Clearinghouses Face for Non-Compliance?
HIPAA penalties vary based on the severity and intent of the violation. OCR (Office for Civil Rights) enforces fines through a tiered system.
Penalty Factors:
- Level of negligence
- Time taken to address the violation
- Scope of impact on PHI
- Number of affected individuals
Penalty Tiers for HIPAA Violations (2024)
| Tier | Description | Penalty per Violation | Annual Cap |
|---|---|---|---|
| Tier 1 | Lack of Knowledge (no reasonable way to know) | 141 to 71,162 $ | $2,134,831 |
| Tier 2 | Reasonable Cause (not willful neglect) | 1,424 to 71,162 $ | $2,134,831 |
| Tier 3 | Willful Neglect (corrected within 30 days) | 14,232 to 71,162 $ | $2,134,831 |
| Tier 4 | Willful Neglect (uncorrected after 30 days) | $71,162 minimum | $2,134,831 |
How Can Clearinghouses Maintain Long-Term HIPAA Compliance?
Sustained compliance requires continuous effort and proactive risk management.
Proactive Compliance Strategies:
- Annual HIPAA training refreshers for all personnel with documented attendance records.
- Continuous security monitoring and automated threat detection via SIEM tools.
- Quarterly audits by independent security firms + internal self-audits.
- Business Associate Agreement (BAA) reviews every 12 months.
Bullet List: Proactive Compliance Strategies
- Real-time threat detection and alerting systems with 24/7 SOC monitoring
- Monthly access control audits + privilege escalation reviews
- Scheduled policy and procedure reviews aligned with regulatory updates
- Annual risk assessments + mitigation plan updates
Frequently Asked Questions (FAQ’s)
1. Are all healthcare clearinghouses considered covered entities under HIPAA?
All clearinghouses are automatically HIPAA-covered entities when processing standard transactions (45 CFR 160.103). They additionally become business associates when handling PHI for other covered entities.
2. How soon must a clearinghouse report a data breach?
- To individuals: Within 60 days of discovery (sooner for states with stricter laws)
- To HHS: Within 60 days for breaches affecting 500+ people; annually for more minor breaches
- To media: Required for breaches impacting 500+ residents of a single state/jurisdiction
3. What data formats must clearinghouses support to comply with HIPAA?
Mandatory ANSI X12 formats:
- 837 (Claims)
- 835 (Payments)
- 270/271 (Eligibility)
- 276/277 (Claim status)
- NCPDP D.0 for pharmacy transactions
4. Can a clearinghouse outsource its HIPAA obligations?
No. While subcontractors may perform services under a BAA, the clearinghouse retains ultimate legal responsibility for compliance (45 CFR 164.314(a)).
5. How do clearinghouses validate HIPAA compliance?
Through:
- Continuous monitoring tools (SIEM, UEBA)
- Annual risk assessments (required by §164.308(a)(1))
- Third-party audits (e.g., HITRUST, SOC 2)
- OCR audit protocols
Related Blogs
Top 10 Clearinghouses in Medical Billing 2025: Best Picks for Fast Claims & Fewer Denials
Glossary of HIPAA & Healthcare Clearinghouse Terms
- ANSI X12 – Standardized EDI format for HIPAA transactions (e.g., 837 for claims, 835 for payments).
- AES-256 – 256-bit encryption standard to protect ePHI at rest.
- BAA (Business Associate Agreement) – Contract ensuring third parties handling PHI comply with HIPAA.
- Breach Notification Rule – HIPAA mandates to report PHI breaches within 60 days (sooner for significant breaches).
- Covered Entity – Organizations (providers, insurers, clearinghouses) bound by HIPAA.
- De-identification – Removing personal identifiers from PHI to exempt them from HIPAA protections.
- ePHI (Electronic Protected Health Information) – Digital PHI (e.g., EHR data, claims).
- EDI (Electronic Data Interchange) – Secure digital healthcare data exchange (e.g., ANSI X12).
- HHS (U.S. Department of Health & Human Services) – Federal agency enforcing HIPAA.
- HITRUST – Security framework certifying HIPAA compliance.
- MFA (Multi-Factor Authentication) – Access control requiring multiple credentials (e.g., password + SMS).
- NCPDP D.0 – EDI standard for pharmacy transactions.
- NPI (National Provider Identifier) – Unique 10-digit ID for HIPAA-covered providers.
- OCR (Office for Civil Rights) – HHS division investigating HIPAA violations.
- PHI (Protected Health Information) – Health data linked to an individual (e.g., name, diagnosis).
- Penetration Testing – Simulated attacks to identify security gaps.
- RBAC (Role-Based Access Control) – Restricts system access by user role (e.g., admin vs. staff).
- Risk Assessment – Annual HIPAA-required analysis of ePHI vulnerabilities.
- SIEM (Security Information & Event Management) – Real-time monitoring tool for PHI access.
- SOC 2 (Service Organization Control 2) – Audit report validating vendor security practices.
- TLS 1.2+ (Transport Layer Security) – Encryption protocol for data in transit (HIPAA-mandated).
- Tokenization – Replacing sensitive data (e.g., SSNs) with non-sensitive tokens.
- UEBA (User & Entity Behavior Analytics) – AI-driven anomaly detection in PHI access patterns.
- WORM (Write Once, Read Many) – Immutable storage for audit logs.


